Welcome to join the passwordless secure authentication environment.
Microsoft announced a public preview of Hybrid Azure AD support for FIDO2-based passwordless sign-in.
The preview delivers users with a fast, easy, passwordless and secure way to access Windows devices and all Azure-connected apps and services.
Microsoft’s passwordless authentication currently supports Windows Hello for Business and FIDO2 security keys. Windows Hello for Business is available for employees using dedicated computers; The FIDO2 security key can be used for both employees who use a dedicated computer and those who may use shared PCs in their workplace.
AuthenTrend is a member of both the FIDO Alliance and the Microsoft Intelligent Security Association (MISA). Our series of security keys include ATKey.Pro and ATKey.Card are fingerprint-based FIDO2 biometric keys. Based on FIDO2 standard, the private key or any fingerprints info would never leave in the security key, or can it be copied or accessed from the device.
If you are interested in any of our ATKeys’ technical details, please feel free to contact us.
Let’s see the process going when a user signs in with a FIDO2 security key: (Read the full version at docs.Microsoft.com)
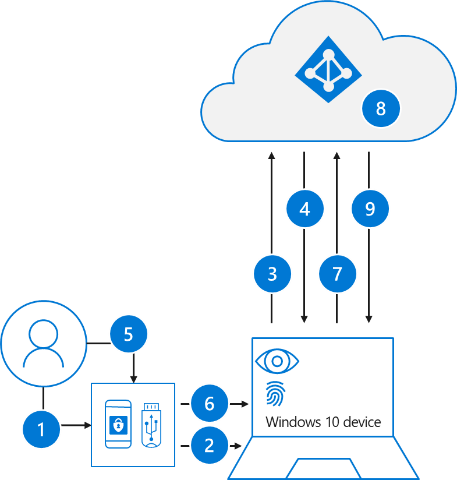

- The user plugs the FIDO2 security key into their computer.
- Windows detects the FIDO2 security key.
- Windows sends an authentication request.
- Azure AD sends back a nonce.
- The user completes their gesture to unlock the private key stored in the FIDO2 security key’s secure enclave.
- The FIDO2 security key signs the nonce with the private key.
- The primary refresh token (PRT) token request with signed nonce is sent to Azure AD.
- Azure AD verifies the signed nonce using the FIDO2 public key.
- Azure AD returns PRT to enable access to on-premises resources.
While there are many keys that are FIDO2 certified by the FIDO Alliance, Microsoft requires some optional extensions of the FIDO2 Client-to-Authenticator Protocol (CTAP) specification to be implemented by the vendor to ensure maximum security and the best experience.
A security key MUST implement the following features and extensions from the FIDO2 CTAP protocol to be Microsoft-compatible:
| # | Feature / Extension trust | Why is this feature or extension required? |
|---|---|---|
| 1 | Resident key | This feature enables the security key to be portable, where your credential is stored on the security key. |
| 2 | Client pin | This feature enables you to protect your credentials with a second factor and applies to security keys that do not have a user interface. |
| 3 | hmac-secret | This extension ensures you can sign in to your device when it’s off-line or in airplane mode. |
| 4 | Multiple accounts per RP | This feature ensures you can use the same security key across multiple services like Microsoft Account and Azure Active Directory. |
Let’s get started!
Please check the important requirements and unsupported scenarios before you start. (Read the full version at docs.Microsoft.com)
Requirements
| Device Type | Azure AD joined | Hybrid Azure AD joined |
|---|---|---|
| Azure Multi-Factor Authentication | X | X |
| Combined security information registration preview | X | X |
| Compatible FIDO2 security keys | X | X |
| WebAuthN requires Windows 10 version 1903 or higher | X | X |
| Azure AD joined devices require Windows 10 version 1909 or higher | X | |
| Hybrid Azure AD joined devices require Windows 10 version 2004 or higher | X | |
| Fully patched Windows Server 2016/2019 Domain Controllers. | X | |
| Azure AD Connect version 1.4.32.0 or later | X | |
| Microsoft Intune (Optional) | X | X |
| Provisioning package (Optional) | X | X |
| Group Policy (Optional) | X |
Unsupported scenarios
The following scenarios aren’t supported:
- Windows Server Active Directory Domain Services (AD DS) domain-joined (on-premises only devices) deployment.
- RDP, VDI, and Citrix scenarios using a security key.
- S/MIME using a security key.
- “Run as” using a security key.
- Log in to a server using a security key.
- If you haven’t used your security key to sign in to your device while online, you can’t use it to sign in or unlock offline.
- Signing in or unlocking a Windows 10 device with a security key containing multiple Azure AD accounts. This scenario utilizes the last account added to the security key. WebAuthN allows users to choose the account they wish to use.
- Unlock a device running Windows 10 version 1809. For the best experience, use Windows 10 version 1903 or higher.
Prepare devices
- Azure Active Directory-joined (AADJ) : Azure AD joined devices that you are piloting during the feature preview must run Windows 10 version 1909 or higher.
- Hybrid Azure Active Directory-joined (Hybrid AADJ): Hybrid Azure AD joined devices must run Windows 10 version 2004 or newer.
- ATKey.Pro / ATKey.Card: FIDO2 Security Key
Enable the use of security keys for Windows sign-in
-
Enable with Intune
To enable the use of security keys using Intune, complete the following steps:
- Sign in to the Azure portal.
- Browse to Microsoft Intune > Device enrollment > Windows enrollment > Windows Hello for Business > Properties.
- Under Settings, set Use security keys for sign-in to Enabled.
Configuration of security keys for sign-in isn’t dependent on configuring Windows Hello for Business.
-
Targeted the Intune deployment
To target specific device groups to enable the credential provider, use the following custom settings via Intune:
- Sign in to the Azure portal.
- Browse to Microsoft Intune > Device configuration > Profiles > Create profile.
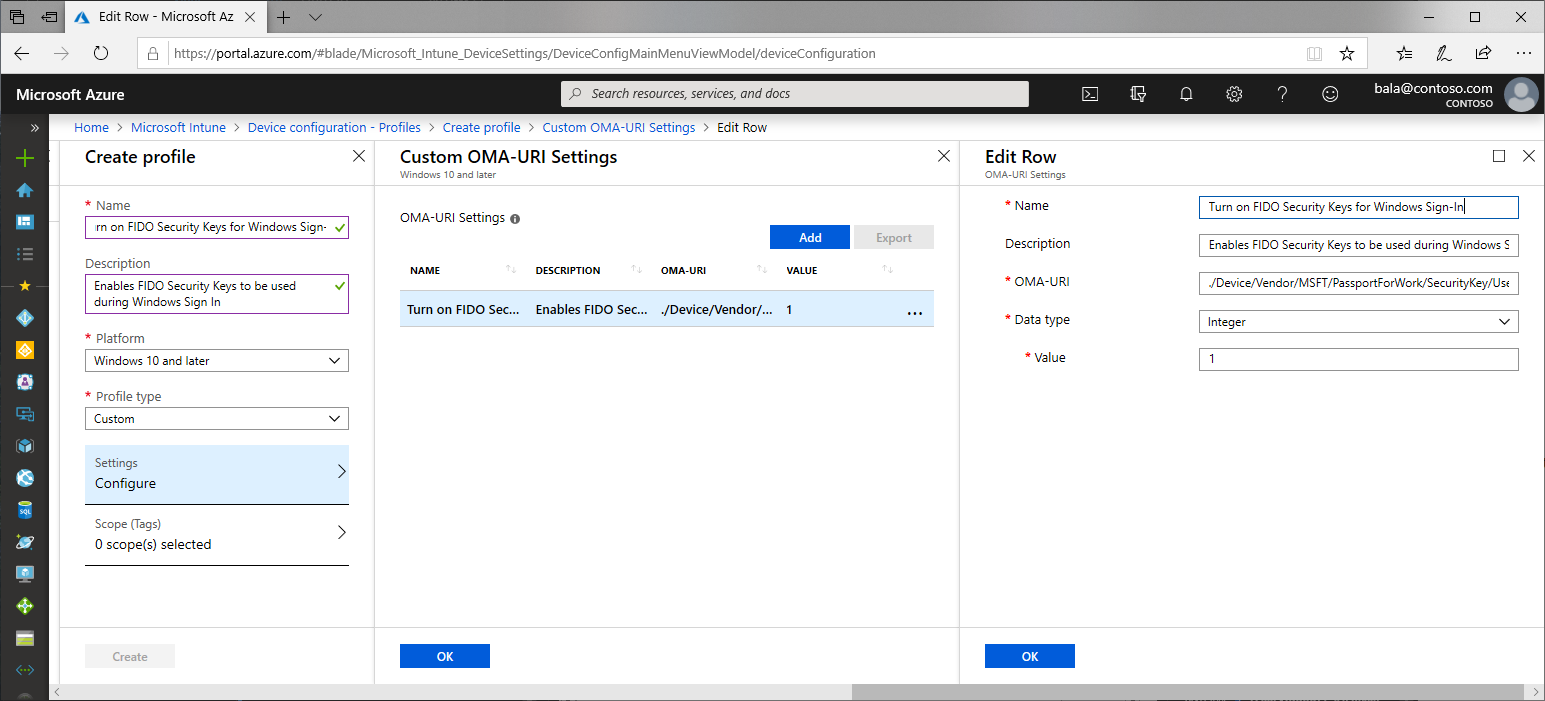
- Configure the new profile with the following settings:
- Name: Security Keys for Windows Sign-In
- Description: Enables FIDO Security Keys to be used during Windows Sign In
- Platform: Windows 10 and later
- Profile type: Custom
- Custom OMA-URI Settings:
- Name: Turn on FIDO Security Keys for Windows Sign-In
- OMA-URI: ./Device/Vendor/MSFT/PassportForWork/SecurityKey/UseSecurityKeyForSignin
- Data Type: Integer
- Value: 1
- This policy can be assigned to specific users, devices, or groups. For more information, see Assign user and device profiles in Microsoft Intune.

-
Enable with a provisioning package
For devices not managed by Intune, a provisioning package can be installed to enable the functionality. The Windows Configuration Designer app can be installed from the Microsoft Store. Complete the following steps to create a provisioning package:
-
- Launch the Windows Configuration Designer.
- Select File > New project.
- Give your project a name and take note of the path where your project is created, then select Next.
- Leave Provisioning package selected as the Selected project workflow and select Next.
- Select All Windows desktop editions under Choose which settings to view and configure, then select Next.
- Select Finish.
- In your newly created project, browse to Runtime settings > WindowsHelloForBusiness > SecurityKeys > UseSecurityKeyForSignIn.
- Set UseSecurityKeyForSignIn to Enabled.
- Select Export > Provisioning package
- Leave the defaults in the Build window under Describe the provisioning package, then select Next.
- Leave the defaults in the Build window under Select security details for the provisioning package and select Next.
- Take note of or change the path in the Build windows under Select where to save the provisioning package and select Next.
- Select Build on the Build the provisioning package page.
- Save the two files created (ppkg and cat) to a location where you can apply them to machines later.
- To apply the provisioning package you created, see Apply a provisioning package.
Note: Devices running Windows 10 Version 1903 must also enable shared PC mode (EnableSharedPCMode).
For more information about enabling this functionality, see Set up a shared or guest PC with Windows 10.
-
Enable with Group Policy (Hybrid AAD joined devices only)
For hybrid Azure AD joined devices, organizations can configure the following Group Policy setting to enable FIDO security key sign-in. The setting can be found under Computer Configuration > Administrative Templates > System > Logon > Turn on security key sign-in:
-
- Setting this policy to Enabled allows users to sign in with security keys.
- Setting this policy to Disabled or Not Configured stops users from signing in with security keys.
This Group Policy setting requires an updated version of the credentialprovider.admx Group Policy template. This new template is available with the next version of Windows Server and with Windows 10 20H1. This setting can be managed with a device running one of these newer versions of Windows or centrally by following the guidance in the support topic, How to create and manage the Central Store for Group Policy Administrative Templates in Windows.
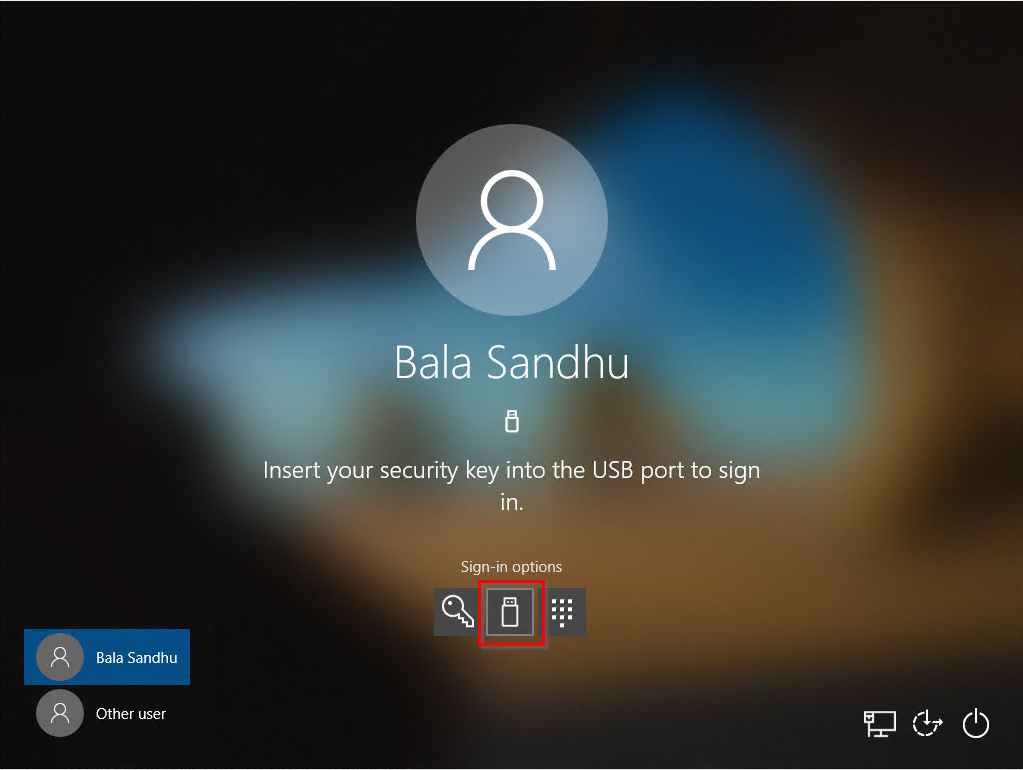

Sign in with ATKeys
-
Enrolling fingerprint(s) with your ATKeyWindows 10 version 1903 or higher
- Users can open Windows Settings on their device > Accounts > Security Key

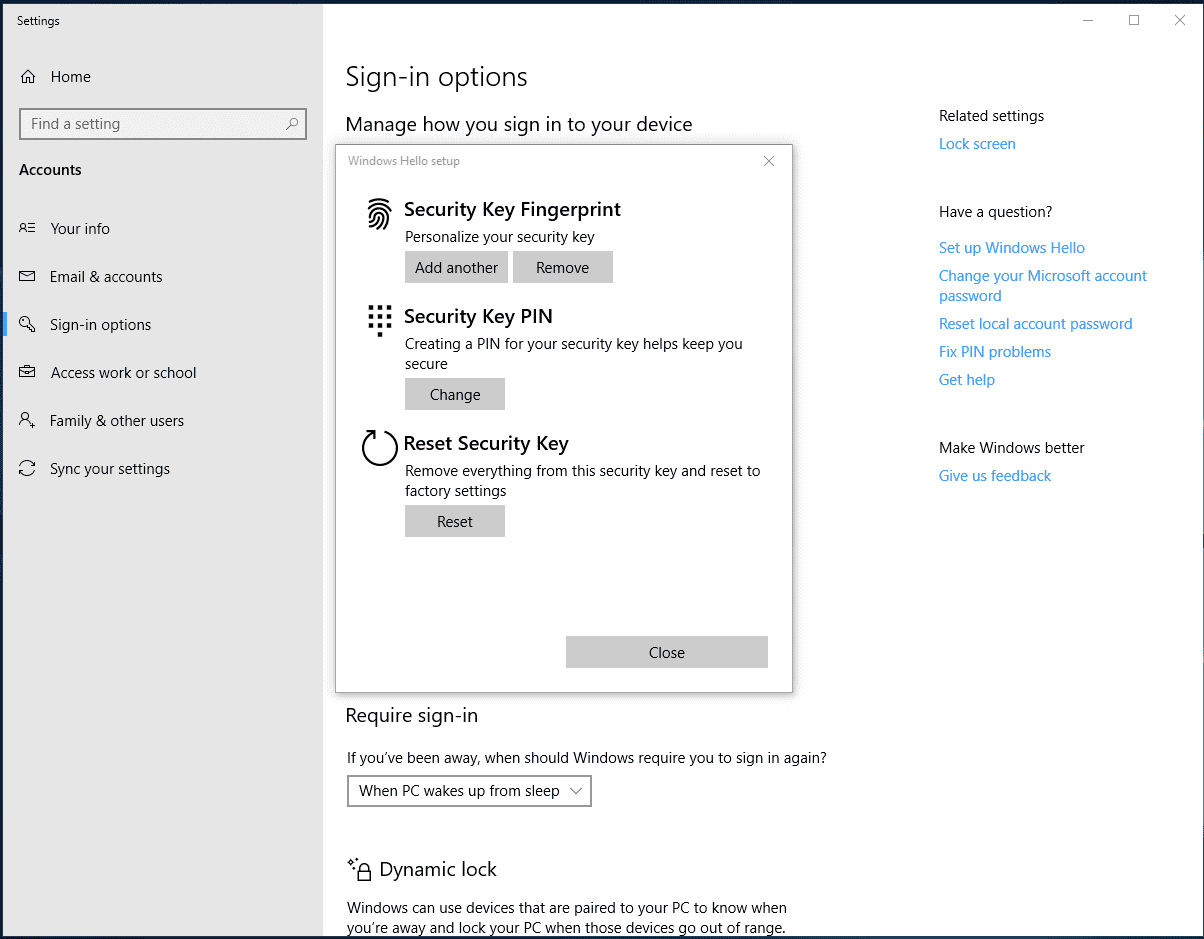
- For first-time use, a PIN code is required for the ATKey
- Users can change their PIN, update biometrics, or reset their security key
- Users can open Windows Settings on their device > Accounts > Security Key
-
Connecting the key with the Windows Azure AD User Account

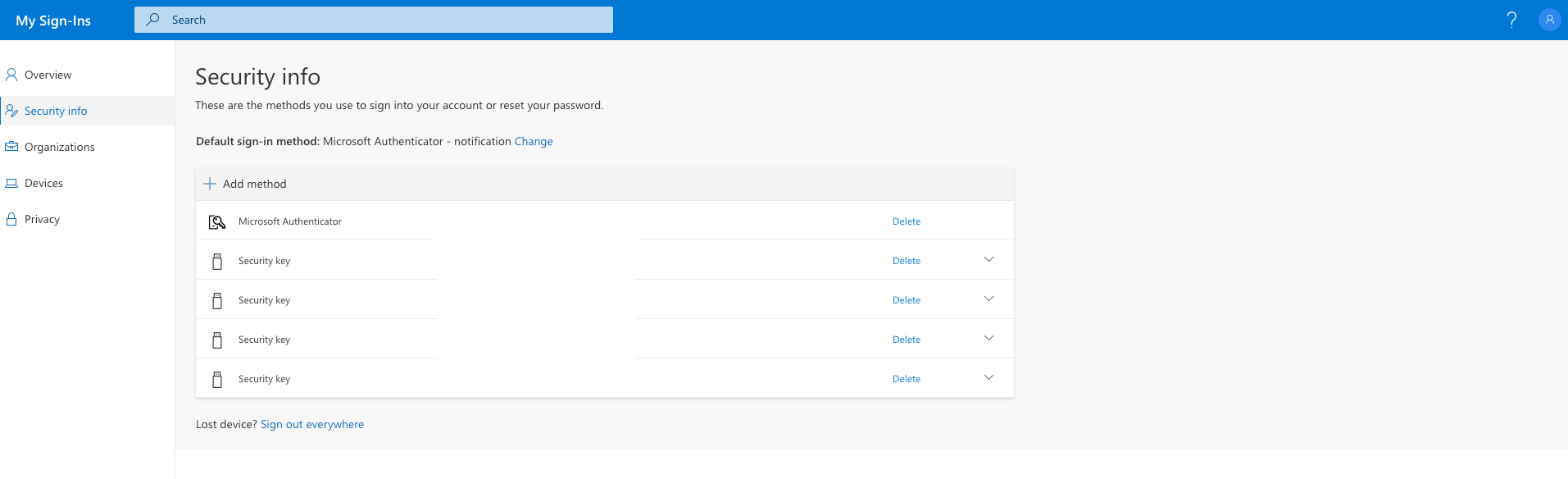
Once logged in, we can seamlessly access Office 365 without further authentication.
Passwordless authentication works in offline scenarios as well.
[video_embed video=”uoSf_B9hTY8″ parameters=”” mp4=”” ogv=”” placeholder=”” html5_parameters=”” width=”700″ height=”400″]
If you are interested in any of our ATKeys’ technical details, please feel free to contact us.
[contact_box title=”AuthenTrend” email=”[email protected]” www=”www.authentrend.com” image=”https://authentrend.com/wp-content/uploads/2020/10/AuthenTrend-Website-C-1.png” animate=””]
